T-Pot Honeypot Dashboard provides a comprehensive framework to collect, visualize, and analyze attack data effectively. This article provides an in-depth look at key visuals from T-Pot’s dashboard, breaking down their meaning and practical applications for enhancing cybersecurity. For newcomers, we recommend exploring What is T-Pot and What is It Used For? and following our step-by-step installation guide.
Attack Map Overview
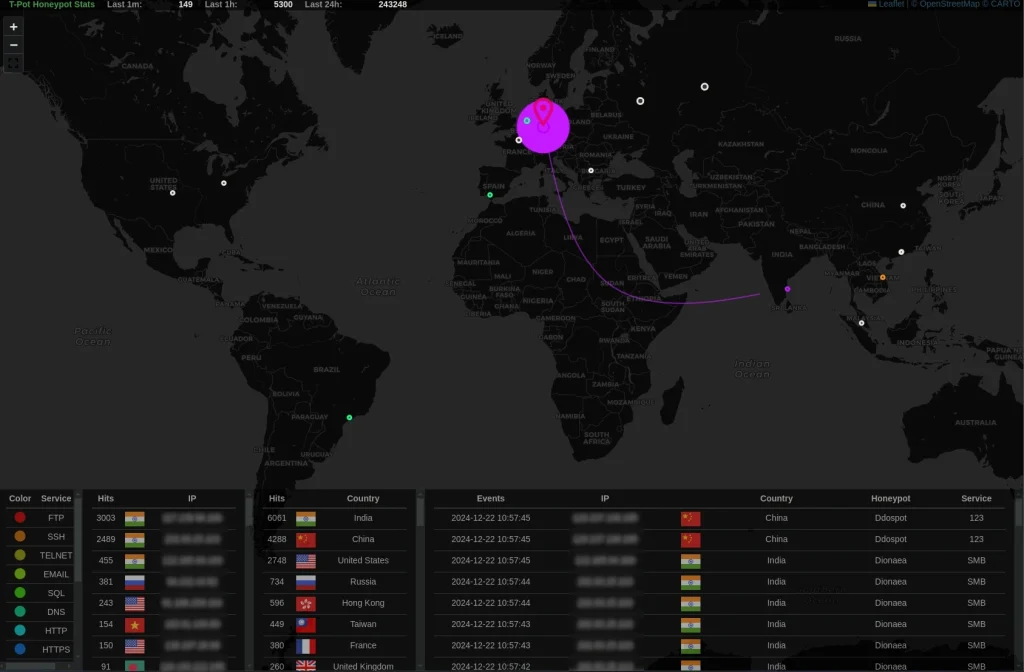
Key Features
- Dynamic Attack Visualization
- The map highlights attack routes in purple lines, connecting attacker locations to your honeypot. Visualizing these routes helps identify attack patterns, assess geographical threat origins, and uncover clusters of coordinated activity. Each line represents an attack attempt.
- Larger purple circles indicate regions with concentrated attack sources, providing insight into potential hotspots of malicious activity.
- Data Tables
- Below the map, tables categorize attacks by service, country, and time:
- Services: Frequently targeted protocols like FTP, SSH, and Telnet are color-coded for easy identification.
- Countries: Lists top attack-originating countries, offering geographical context.
- Hits: Reflects how often specific services or countries are targeted, enabling organizations to prioritize defenses effectively.
- Below the map, tables categorize attacks by service, country, and time:
Significance
The attack map is a vital tool for recognizing trends in attack origins, identifying commonly targeted services, and analyzing attack frequency. Organizations can use this data to implement region-specific defenses or monitor high-risk services.

Unleash unparalleled performance with the Raspberry Pi 5, featuring a powerful quad-core ARM A76 processor. It’s the ultimate platform for advanced computing and creative projects.
Tagcloud Insights
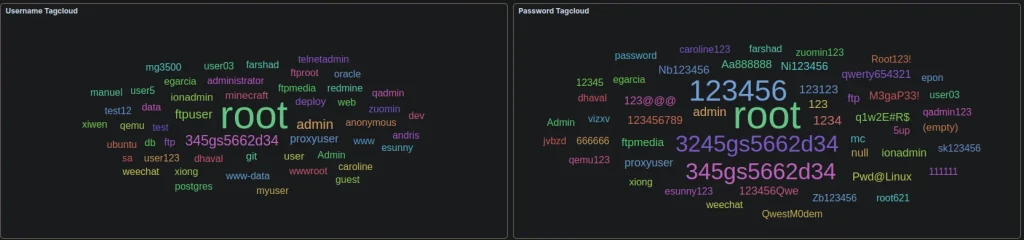
Username and Password Tag Clouds
These tag clouds aggregate data from brute-force attacks, showing the most commonly attempted usernames and passwords.
- Username Tag Cloud:
- The prominence of “root” indicates frequent targeting of default administrative accounts.
- Other usernames like “admin,” “minecraft,” and “postgres” suggest attackers also exploit misconfigured applications.
- Password Tag Cloud:
- Weak passwords such as “123456,” “password,” and “admin” dominate the tag cloud.
- Numeric sequences and default passwords highlight attackers’ reliance on predictable credentials. Organizations can use this insight to enforce complex password requirements and audit accounts regularly.
Significance
The tag clouds emphasize the importance of strong password policies and disabling default accounts. By analyzing these patterns, administrators can proactively detect vulnerabilities and mitigate brute-force attacks.
Elastic Stack Overview
The Elastic Stack Dashboard consolidates data from the T-Pot Honeypot Dashboard into actionable insights through intuitive visualizations.
Top Panels
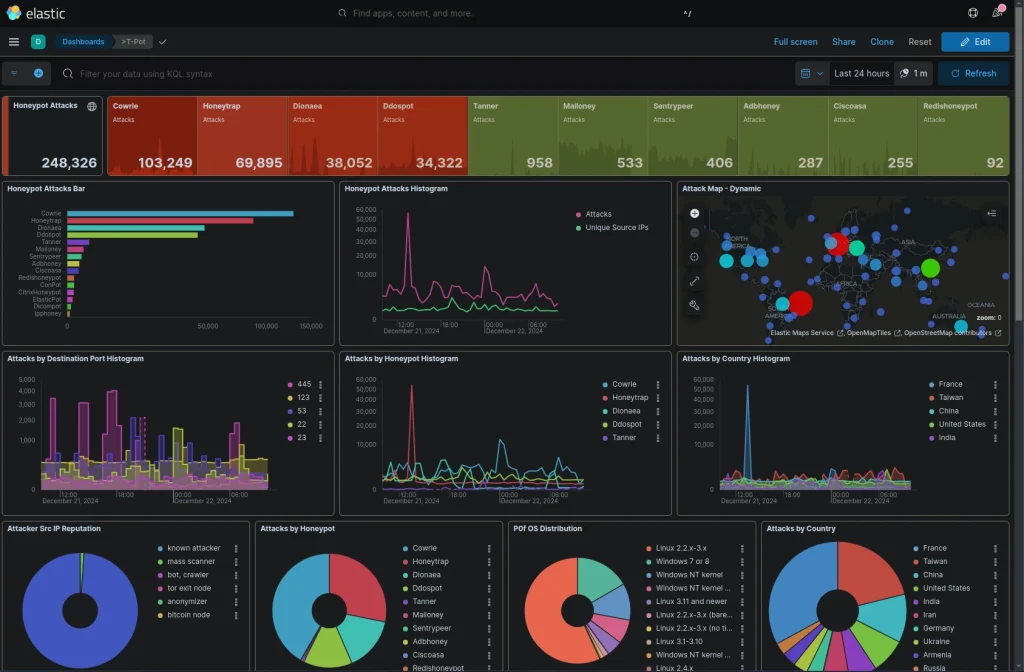
- Total Honeypot Attacks:
- Displays the total attack count, categorized by honeypot type (e.g., Cowrie, Dionaea).
- Highlights which honeypots attract the most activity, providing a clear view of attack trends.
- Attack Sources:
- Identifies the most common attacker IPs and their geolocations.
- Pinpoints coordinated attacks or regional attack clusters.
Graphs and Histograms
- Honeypot Attacks Bar Chart:
- Compares attack volume across different honeypots, revealing the most targeted protocols.
- Destination Port Histogram:
- Displays frequently targeted ports (e.g., 445, 123), helping identify potential vulnerabilities.
Pie Charts
- Attacker Source Reputation:
- Categorizes sources as bots, crawlers, or anonymizers, offering insights into attacker tactics.
- Attacks by Honeypot:
- Visualizes attack distribution across honeypots, showing which ones capture the most activity.
Significance
The Elastic Dashboard simplifies cybersecurity monitoring by presenting attack trends, enabling real-time threat detection, and identifying areas for security improvement.

Protect your Raspberry Pi in style with the GeeekPi Aluminum Case, offering premium heat dissipation and durability. Complete with thermal stickers, it ensures optimal cooling for demanding applications.
Using Dashboard Insights Effectively
The data collected by T-Pot enables proactive security enhancements. Here are actionable ways to utilize these insights:
- Strengthen Password Policies:
- Use tag cloud data to enforce strong, unique password policies.
- Disable or rename default accounts such as “root” and “admin” to reduce attack surfaces.
- Harden Vulnerable Services:
- Restrict access to critical services like SSH or FTP based on observed attack trends.
- Apply rate-limiting or geofencing for high-risk regions.
- Deploy Network Defenses:
- Create firewall rules using attacker IPs and reputation data.
- Optimize intrusion detection systems (IDS) by analyzing frequently targeted ports.
- Improve Incident Response:
- Leverage historical data to simulate attack scenarios and refine response strategies.
- Use real-time dashboards to detect coordinated campaigns and emerging threats.
How Public Honeypots Enhance Security
Public honeypots like T-Pot play a significant role in improving global cybersecurity:
- Raising Awareness:
- By visualizing real-world attacks, T-Pot educates organizations on the scope and nature of cyber threats.
- Shared data fosters collaboration among security researchers and professionals.
- Threat Intelligence Sharing:
- Aggregated honeypot data helps uncover large-scale attack trends, identify new malware, and detect botnets.
- Shared intelligence enables faster responses to emerging threats.
- Testing and Development:
- Security teams use honeypot data to evaluate defenses and refine detection tools.
- Developers gain insights into vulnerabilities in widely used software and protocols.
- Deterring Attackers:
- Knowing honeypots monitor and report malicious activity increases the risks for attackers, deterring opportunistic exploits.
Conclusion
The T-Pot Honeypot Dashboard’s visualizations and analytics transform complex attack data into actionable insights. Its ease of use, integration with Elastic Stack, and comprehensive visualizations make it a standout honeypot solution. Whether safeguarding a homelab or an enterprise network, T-Pot simplifies cybersecurity monitoring and strengthens defenses. Start exploring T-Pot today to elevate your security strategy and stay ahead of evolving threats.

Power your Raspberry Pi with reliability and efficiency using the official Raspberry Pi Power Supply. Designed to deliver consistent performance, it’s the ideal choice for your projects.



